Which Method Is Used to Check the Integrity of Data
Checks test correctness of data transformation. Validation rules validate if the data is unique specified and within a range.
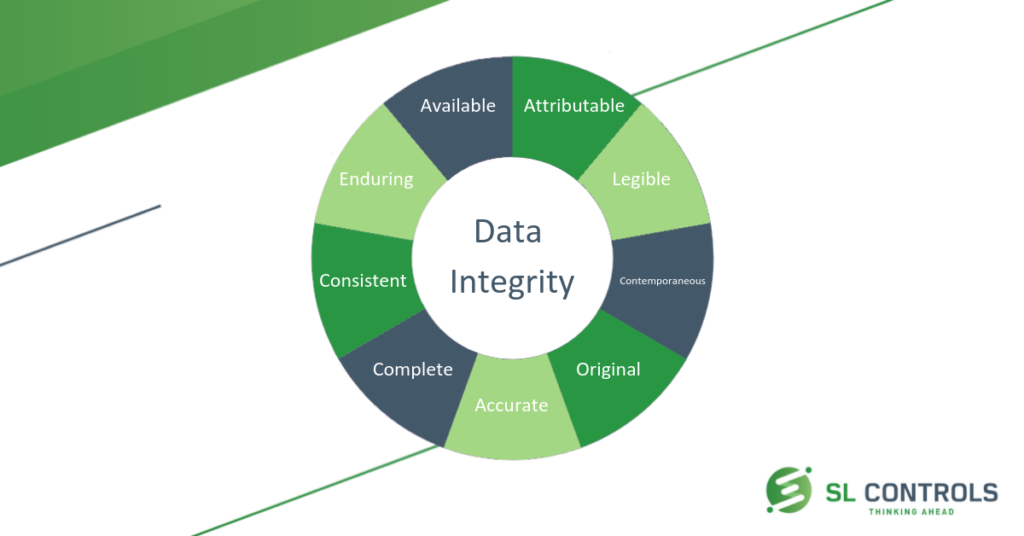
What Is Alcoa And Why Is It Important To Validation And Data Integrity Sl Controls
After the data is received the checksum hashing is performed again.

. Which method is used to check the integrity of data. Credit card or bank routing numbers. We also achieve this in a manner in which a digital proof stamp can be made visual to help achieve virality for the end users.
Checksum backup authentication encryption Explanation. The common methods used for data integrity check include. These are used to maintain data integrity after manual transcription from one computer system to another by a human intermediary eg.
Focus on data validation to ensure the accuracy of data when collected or integrated. Data integrity can be verified by comparing the stored and the newly computed values on every. An integrity check program with built-in intelligence is the only solution that can handle all.
Checksum backup authentication encryption A checksum value of a block of data is calculated and transmitted with the data. Sometimes the hash is called a check digit if it only consists of one digit. When a referential integrity constraint is violated normal procedure is to.
Select Appropriate System and Service Providers 3. Which method is used to check the integrity of data. This research outlines a method in which integrity authentication and provenance can be established for raw data within a file even when the metadata attached to it has changed.
3 Checksums and CRCs Protect Data Integrity Compute check sequence when data is transmitted or stored Data Word. Checksumming is a well known method for performing integrity checks. This is the case for barcodes ISBN numbers and credit card numbers where the last digit of the code is a check digit the.
This research outlines a method in which integrity authentication and provenance can be established for raw data within a file even when the metadata attached to it has changed. Perform Risk-Based Validation 2. Make political statements or create fear by causing physical or psychological damage to victims.
A checksum value of a block of data is calculated and transmitted with the data. After the data is received the checksum hashing is performed again. 8 Ways to Ensure Data Integrity Vaisala Page Sections Introduction 1.
Maintain a regular backup of data. Data users in various application domains want to be ensured that the data they are consuming are accurate and have not been tampered with. Limit access to data and change permissions to constrain modifications to data by unapproved parties.
Human-induced data integrity errors are often detected through the use of simpler checks and algorithms such as the Damm algorithm or Luhn algorithm. Data can be tampered with and malicious actors could use this to their advantage. Qualify IT Validate Systems 6.
The calculated value is compared with the transmitted value to verify the integrity of the data. Event handlers use microflows to provide custom logic to validate data. We also achieve this in a manner in which a digital proof stamp can be made visual to help achieve virality for the end users.
The result of the CRC or checksum calculation Code Word Data Word with Check Sequence Appended To check data integrity. It focuses on-Check foreign primary key integrity. Integrity checking products work by reading your entire disk and recording integrity data that acts as a signature for the files and system sectors.
Plan for Business Continuity 7. Which method is used to check the integrity of data. Audit your Audit Trails 4.
The hash of a hashing algorithm used for integrity validation is often called a checksum and is appended at the end of the data to be transferred. Which method is used to check the integrity of data. Even the slow hash functions eg.
The data you want to protect can be any size. Data integrity is all about keeping the garbage data out. The following is used to uniquely identifies the element in relation.
Checksums can be computed for disk data and can be stored persistently. After the data is received the checksum hashing is performed again. Retrieve or receive Code Word.
Data integrity refers to the reliability and trustworthiness of data throughout its lifecycle. ETC Source and Data Integrating Test This test is used to examine most of the tests and evaluate most Data Integrity. It can describe the state of your dataeg valid or invalidor the process of ensuring and preserving the validity and accuracy of data.
Which statement describes cyber warfare. Also used to verify all valid invalid conditions then subsequently we proceed for source and targeted data. Often Mbytes Check Sequence.
Mendix supports different methods to ensure the integrity of your application data. Checksum backup authentication encryption Answers Explanation Hints. Access rules ensure only authorized.
Reading the file will be the bottleneck not hashing it a 24 GHz PC can hash data with SHA-512 at a speed close to 200 MBs using a single core. Use logs to monitor when data is entered altered or erased. A user can insert update or delete the values in a Database and in order to restrict or constraint the users data integrity can be enforced.
A checksum value of a block of data is calculated and transmitted with the data. To validate the integrity of these data we describe a blockchain-based hash validation method. SHA-256 will run faster on a typical PC than the harddisk.
Error checking and validation for example are common methods for ensuring data integrity as part of a process. Data integrity refers to the correctness and completeness of data with respect to a database. Method used to check for integrity of data in a Request object.
1HttpRequestValidateInput 2HttpRequestCurrentValidate 3HttpRequestValidateUserInput 4HttpRequestValidate. Numeric columnscells in a table. It is Internet-based conflict that involves the penetration of information systems of other nations.
Data types ensure only valid data types can be stored. Hash function performance is unlikely to be an issue. An SQL standard Allows a clause initially deferred to be added to a.

Database Testing Complete Guide Why What And How To Test Data

0 Response to "Which Method Is Used to Check the Integrity of Data"
Post a Comment